Static Proxy vs Dynamic Proxy: What’s the Difference?
Proxies, both static and dynamic, serve as gatekeepers between users and the internet. Do you know which one is more suitable for your project? In this article, we will explore the differences between them, discussing their benefits and limitations. Furthermore, we will list the applicable scenarios for each type to help you choose the right one for your needs.
What is a Static Proxy?
In computer network terms, a static proxy is a type of internet intermediary that provides a constant IP address for your online activities. This fixed IP remains the same over multiple sessions, all your request will be routed through it, which masking your real location and details from the web. It’s a reliable choice for tasks that require a consistent identity.
How Do Static IP Proxies Work
If you choose a static proxy, the server provider will allocate a dedicated IP address to you. When connecting to the internet through it, your online requests are first sent to the proxy server. The server then forwards these requests to the web using the dedicated IP address allocated to you. Any responses are collected by the proxy server and then sent back to you.
Characteristics of Static Proxy
1. Fixed IP Address
The main feature of a static proxy is its fixed IP address, which provides a stable online identity. It avoids the situation where your IP address seems to jump from the southern hemisphere to the United States overnight. As a result, your access requests appear to come from a regular user, not someone trying to hide their identity.
2. High Link Stability
With a static IP proxy, the connection is more stable because the risk of blacklisting or blocking is reduced. If you need to use a proxy to log in to an account, the fixed IP also helps prevent account logout issues caused by network disconnection, an occurrence that can happen during the frequent IP changes characteristic of dynamic proxies.
3. Good IP Reputation
Static proxies often have a strong IP reputation, beneficial for accessing websites that monitor for suspicious activity. Their reliability makes them well-suited for high-trust tasks, such as managing sensitive data.
4. Controllable IP Address Duration and IP Traffic
Users of static proxies can control how long to use an IP address and monitor their traffic, which is advantageous for planning and security purposes. This avoids the situation where your session is interrupted when you are performing data transfer or transaction processing.

What is a Dynamic Proxy?
A dynamic proxy is also a type of internet intermediary, commonly referred to as a rotating proxy. Unlike static proxies, its IP address changes frequently, and its lifespan is short, sometimes only a few hours. When an IP address expires, the system automatically provides you with a new one. This type of proxy is excellent for short-term tasks involving multiple targets or websites that require frequent changes of IP addresses.
How Do Dynamic IP Proxies Work
The service provider maintains a vast pool of IP addresses from various Internet Service Providers (ISPs) globally. These addresses are dynamically allocated to users to meet diverse access requirements and prevent blocking.
Upon connection through a dynamic proxy, the server changes the proxy IP address after each session or when a preset interval elapses. Providers also continuously monitor the performance and response speed of their IPs, swiftly replacing any that are degraded or blacklisted with new ones from the pool.

Characteristics of Dynamic Proxy
1. High Flexibility for Performing Multiple Tasks
When using a dynamic proxy, you obtain IP addresses from a constantly changing pool, with each request potentially using a different IP. This avoids making too many requests from the same IP address, thereby reducing the risk of IP bans.
When you need to access networks in multiple regions, there is no need to pay separately for each IP address. The costs are usually included in the total fee for the proxy service, saving you time and resources in managing and maintaining IP addresses. The flexibility of dynamic proxies makes them particularly suitable for projects that involve multiple short-term tasks.
2. Wide Coverage
These proxies cover a broad range of IP addresses from various countries and regions. This wide coverage makes them suitable for global operations, like aggregating content from diverse geographies.
3. Short Survival Time
The IP addresses used in dynamic proxies have a short lifespan.They come with both benefits and drawbacks: the benefit is that frequently changing IPs can hide your real IP activity, but the drawback is that they are often prone to broken links and interrupted sessions.
4. More Secure
Dynamic proxies enhance security by regularly changing IP addresses. This constant change makes it difficult for malicious entities to track and target your activities, thereby preventing your true IP from being exposed to cyber threats such as DDoS attacks, hacking, and identity theft.
5. Automatically Switch IP Addresses if an Exception Occurs
If there is an issue, such as when a server becomes unreachable, the dynamic proxy automatically switches to another IP address without the need for the user to manually change through complex operations.
6. Good Compatibility and Easy Integration
Due to their automatic IP rotation feature, dynamic proxies can quickly adapt to changes in the network environment. Additionally, they are compatible with a wide range of operating systems and applications, making them easier to integrate.
For users requiring web crawling or data scraping, dynamic proxies typically offer a variety of API interfaces, enabling easy access to and retrieval of proxy IPs.
Static Proxy vs Dynamic Proxy: What’s the Difference?
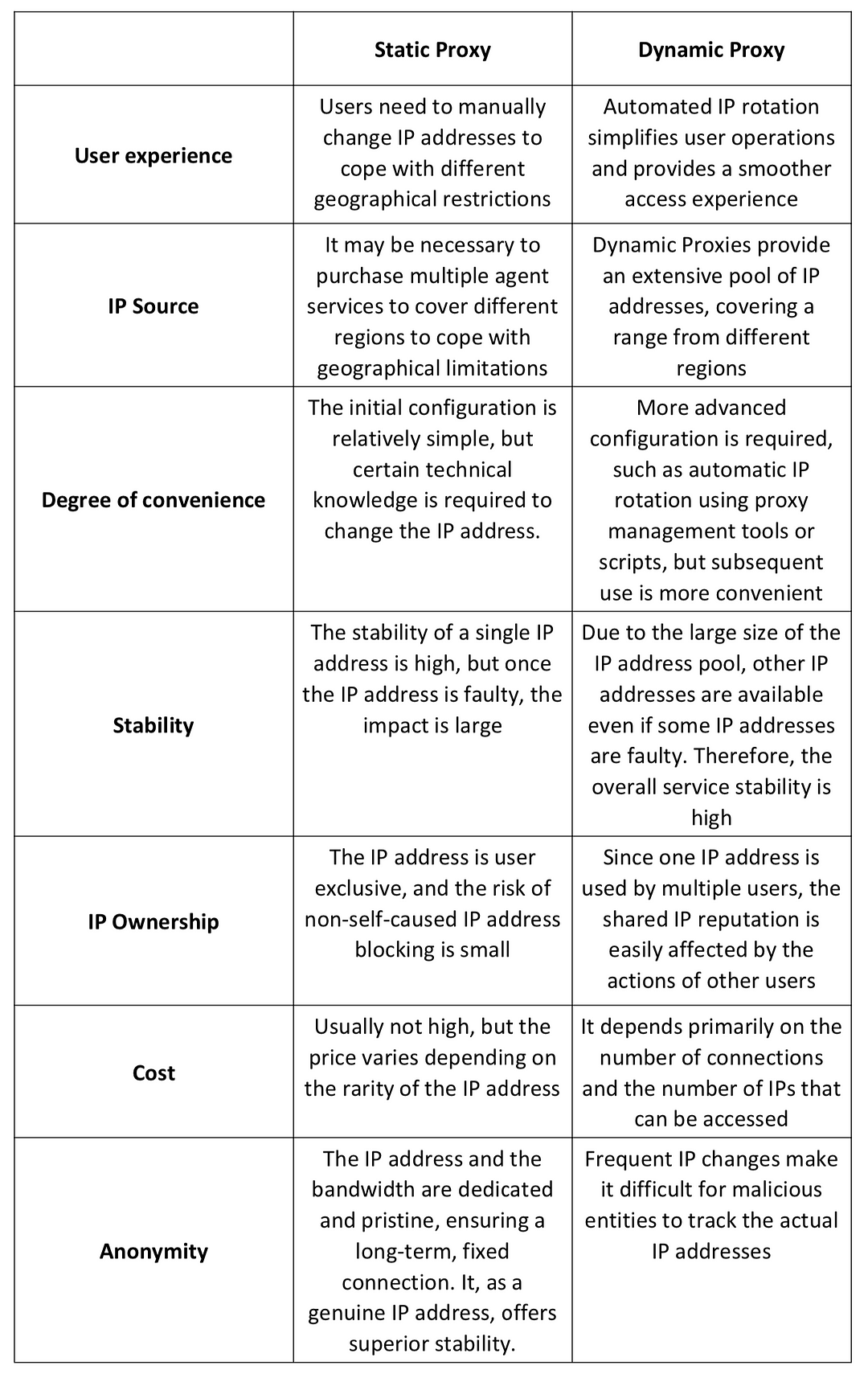
In order to more intuitively see the difference between them, we have made the following table for reference:
When to Choose Static Proxy or Dynamic Proxy?
Universal Applications
1. Access Geographically Restricted Content
You can use both static and dynamic proxies to see content that is blocked in certain areas. But they work best for different situations. For example, Dynamic proxies are great if you want to play games that are only available in other countries. They make it seem like you’re in a different place, getting around the blocks. Static proxies are better when you need to access sites that require login and are geographically restricted. They give you the same IP address every time, so the website knows you’re the same person.

2. Web Crawls
When performing web crawling tasks, both types of proxies can be helpful. The key is knowing which one to use. Static proxies are ideal for crawlers or automated scripts that simulate user behavior. They keep your IP address the same, so you don’t get noticed by the websites you visit. Dynamic proxies are better for collecting lots of information at a high frequency. By frequently changing your IP address, you can mask the crawler’s activities and reduce the risk of being blocked by web servers.

Tasks Suited for Static Proxies
1. E-commerce and Social Media Marketing Business Correlation
Many e-commerce platforms like Amazon and Discord, as well as social media sites such as Facebook, TikTok, and Instagram, monitor account IP addresses to detect anomalies. Using a dynamic proxy can cause your login IP’s geographic location to jump around too much, which may lead to account bans. Therefore, for these purposes, it’s best to use a single, stable IP address, which is what a static proxy provides.
2. Protect the Privacy and Security of Important Accounts
If you are primarily concerned with security and wish to protect important accounts such as bank accounts, it is best to use a static proxy that provides a dedicated IP. This ensures a stable connection and significantly reduces the risks associated with IP address changes.
3. Tasks Requiring Good IP Credibility
As we mentioned above, a static proxy offers you an exclusive IP address, preventing you from being influenced by other users’ bad behavior and maintaining good IP credibility. It’s essential for actions that need to imitate real human behavior.
For example, if you need to collect industry market data for analysis, an authentic online identity will help you obtain accurate and timely financial data without triggering the website’s gateway alerts. However, it is crucial to ensure that data collection is conducted within legal limits.
Moreover, when online education and research institutions access academic resources or conduct remote testing, using a highly reputable static proxy can ensure the stability and reliability of access.
Tasks Suited for Dynamic Proxies
1. Verify the Effectiveness of Advertising in Different Areas
Dynamic proxies are perfect for marketing teams that need to test ad effectiveness across different regions. They allow you to view content as if you are based in various locations, providing genuine feedback on regional advertising strategies for better optimization.
2. Market Price Comparison and Competitive Intelligence Gathering
If you need to compare prices in different regions or understand the strategies of competitors in different areas, you can simulate access requests from different regions through dynamic IP proxies, which can help you collect useful information.
3. Optimize SEO Ranking
Using dynamic proxies is a valuable approach to search engine optimization. They enable you to view search results from various regions, helping you grasp regional ranking nuances. This understanding is crucial for effectively optimizing your SEO strategy.
Conclusion
Congratulations! Having read this far, you must have gained a comprehensive understanding of both static and dynamic proxies and learned how to make choices based on your actual business needs. But then again, how can you verify the quality of the proxies you are using?
Here’s a convenient solution: use BrowserScan to check whether your real IP address is leaked. It is a user-friendly, precise web-based tool that provides an interface where you can immediately see various pieces of your network information, as well as the authenticity of the browser fingerprint they collectively create, helping you easily assess the status of your online identity.”