Guide to IP Whitelisting: Everything You Need to Know
Whether you're a business or an individual, using the internet for communication, data storage, and transactions is essential. However, with the rise of cloud services and remote work, the challenges of cybersecurity are ever-changing, and traditional defenses are no longer enough. Mastering and using IP whitelisting has become an important strategy to ensure safe remote connections and keep data confidential.
This article will dive into what IP whitelisting is, how it works, its importance, and its limitations. By reading this, you'll gain a practical guide to achieving a higher level of cybersecurity.
What is an IP Address?
An IP address is a unique set of numbers assigned to a device or network. It's made up of numbers separated by periods.
Examples:
192.168.0.1
127.0.0.1
2001:db8::1
The IP address ensures that information is accurately delivered to the right destination on a network, similar to a house number in the digital world.
There are mainly two types of IP addresses: IPv4 and IPv6. IPv4 is the most widely used version currently, while IPv6 is the next generation format designed to address the potential exhaustion of IPv4 addresses.
You can use BrowserScan's IP address lookup to find out your IP address information.
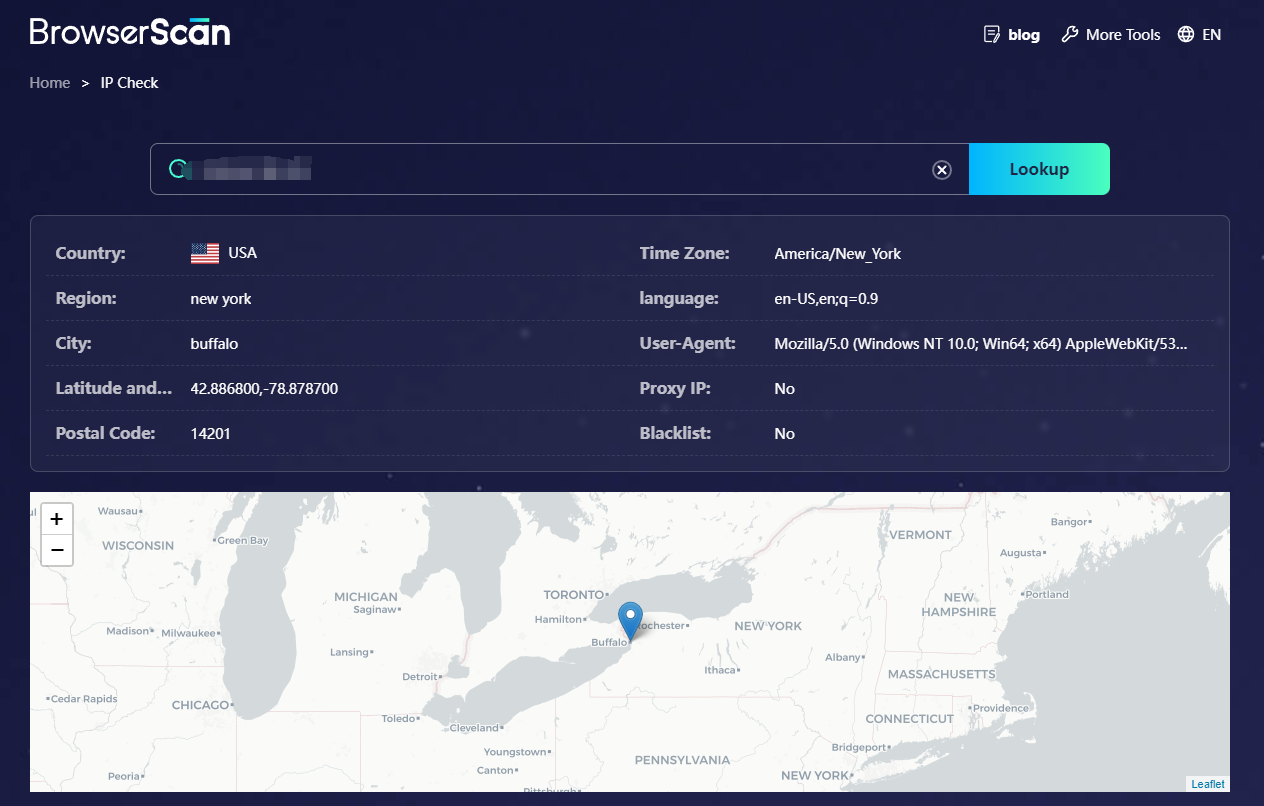
Static vs Dynamic IP Addresses
IP addresses come in two types: static and dynamic. A static IP address remains constant once it's assigned to a device or network, making it ideal for situations that require long-term, stable communication.
In contrast, dynamic IP addresses change as devices connect and disconnect, which is more suitable for individual users and some business networks. These are assigned by Internet Service Providers (ISP) and offer more flexibility.
What is an IP Whitelist?
An IP whitelist is a cybersecurity technique that allows IT admins to control "who" can access systems and resources. By creating a list of trusted IP addresses (usually static), and assigning them to users or groups, only these IP addresses are permitted to access the target server.
Thus, any system within a Local Area Network (LAN), data center, or third-party SaaS application can be set to be accessible only by whitelisted users. Regardless of whether users connect via a private network or a VPN gateway, only whitelisted IP addresses can access the system, while non-whitelisted IP addresses are restricted.
How IP Whitelisting Works
In the internet, a local network, or a private virtual network, communication between servers and clients is transmitted in the form of data packets. Each packet contains a source IP address and a destination IP address. These addresses are public, telling internet routers where to send the packet. When the packet reaches the destination device or server, it reads the source address. If the source is whitelisted, the destination accepts the packet; if not, the destination rejects the packet, notifying the sender of the denied access or simply dropping the packet.
With whitelisting:
Only whitelisted users can remotely access your business systems.
Anyone trying to access your systems from anywhere will be immediately blocked.
Your remote business operations are protected.
Your private business information is kept safe.
How to Whitelist an IP Address?
To create an IP whitelist, you first need to decide which devices and users should have access to your business systems. You can add them to the whitelist through network settings on your computer, router, or firewall. The specific steps might include configuring the router to create a whitelist or editing firewall rules, depending on your setup and security requirements.
This process is similar to making a guest list for an event you're hosting and giving it to the venue's security to manage admission. Only those on the list can enter the event, while others are restricted.
IP whitelists are typically set up in:
Firewalls
Edge Routers
Business VPN Gateway
Web Server
Application Layer
SaaS Application
Benefits of IP Whitelisting
For businesses, protecting software, systems, and stored data is crucial. They need to ensure that only authorized employees can access sensitive information. At the same time, to support remote workers, it's important to ensure that they can safely access these systems. IP whitelisting helps in both respects and brings the following practical benefits to your business:
Enhanced Cloud Security
IP whitelisting prevents unauthorized access to the network by IP addresses not on the whitelist, thus enhancing the security of cloud environments.
Increased Productivity
Insecure websites can reduce work efficiency and impact company profits. IP whitelisting is a simple and effective method to block most dangerous connections, supporting business continuity and boosting productivity.
Secure Remote Access
Users connect to gateways through client applications installed on specific devices. After authentication, they are allowed to access certain systems. In this case, connections from any device that can successfully log in are protected.
Cost Reduction
You can securely use public internet connections without the need to build your own network.
Limitations of IP Whitelisting
While IP whitelisting has clear advantages for enhancing network security, it also has its limitations.
Time-Consuming and Repetitive
For IT administrators who manage large networks with many users and devices, creating a whitelist is a complex task. They must carefully decide who gets access and which IP addresses to allow, and then manually set this up on firewalls and routers. A whitelist that is too strict can interfere with normal business activities, while one that is too loose may not provide enough security. Also, when user roles or access rights change often, it takes extra work to update the whitelist.
Better for Smaller Networks
The size of the network directly affects how hard it is to maintain an IP whitelist. The larger the network, the harder it is to keep up, which might lead to unauthorized connections slipping through unnoticed. In fact, IP whitelists are more suitable for small organizations with less data traffic. Larger organizations need to segment their networks internally, grouping users based on the source address of their IP packets for more fine-tuned access control.
Ignoring the Source of IP Addresses
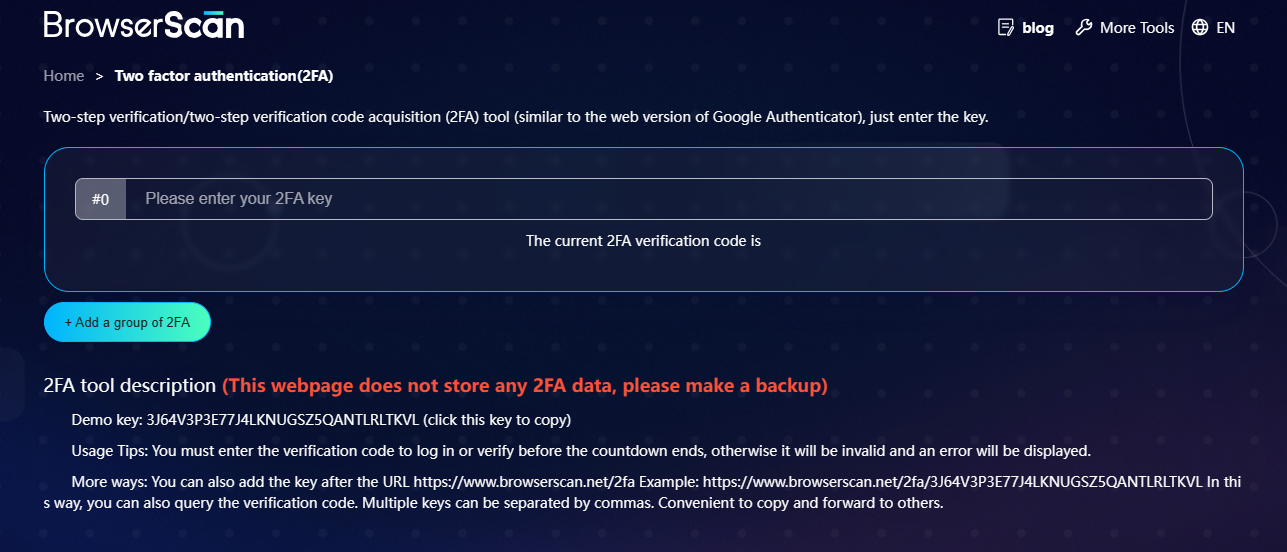
Hackers can fake IP addresses, pretending to be authorized users to bypass the whitelist and break into network systems. This shows a limitation of IP whitelists: they don't check if the actual person using the IP address is trustworthy. Businesses must use additional security measures, like two-factor authentication (2FA) and device ID checks, to prevent such deception.
Click to use BrowserScan's two factor authentication(2FA) .
Unsuitable for Dynamic IP Addresses
Internet Service Providers (ISPs) periodically change IP addresses, so these addresses are constantly shifting. In this case, setting a static IP whitelist won't work because an IP address assigned to someone today could be reassigned to someone else in the future. This could allow new users easy access to an organization's network. Also, it's unrealistic to expect network administrators to manually update the IP address for each new session every time.
Access Barriers
The flaw with IP whitelists is that they block not only unwanted connections but also can restrict our own team members. In urgent situations, if new IP addresses can't be added to the whitelist in time, team members might not be able to establish necessary connections. Therefore, we need a practical emergency plan to ensure quick restoration of resource access without compromising security levels.
Wrapping It Up
While IP whitelists have clear advantages in network security management, they also present practical challenges. To make the most of IP whitelists, we must combine them with other tools to create a more secure and reliable cyber environment. You can use BrowserScan's IP address lookup tool to find out your geographical location and whether you are using a VPN or proxy service, which helps ensure the security of your network connection and protect your privacy.